
Cybersecurity-as-a-Service
Results-driven approach to cybersecurity.
Every business is unique, your security program
should be as well.
A Program Tailored to Your Unique Business Needs
Every 39 seconds, a cybersecurity attack occurs. In the event of a data breach, the consequences can be severe, including financial losses, legal liabilities, reputational damage, or even a complete business shutdown. From ransomware and phishing attacks to IoT, cloud, machine learning, and AI attacks — not to mention software vulnerabilities — businesses face a wide range of cyberthreats that require proactive and effective information security measures to mitigate.
At Cyber Defense Group, our sweet spot is designing Cybersecurity as a Service to help you stay one step ahead of today’s increasingly complex cybersecurity landscape and keep your business safe as you scale and grow. Our full-service cybersecurity Image team will help you strengthen your security posture so your business can proactively monitor, prevent, identify, investigate and respond to cyberattacks, 24/7.
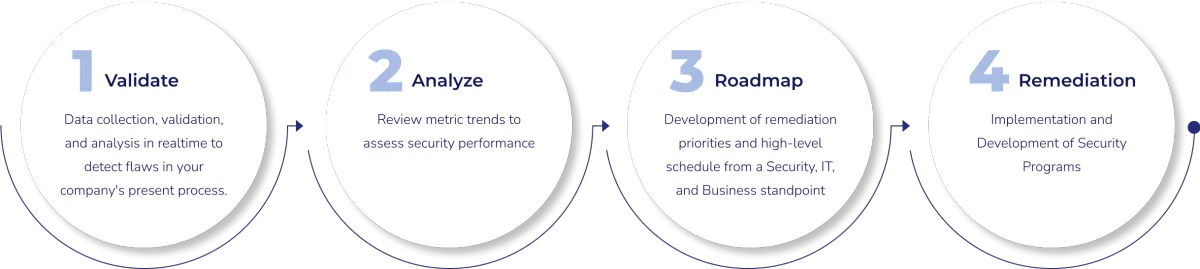
How Cybersecurity as a Service Works
We work closely with you to understand your goals and priorities, then complete a comprehensive security assessment. Our findings are compared against regulatory and security frameworks to identify potential vulnerabilities and areas for improvement. From there, we design a customized security program that aligns with your needs — and rather than racking up billable hours, we outline a fixed-cost program to get you where you need to be.
This is not your typical consulting engagement. We train and work closely with your internal teams to ensure your growing business is equipped with the highest cybersecurity posture to safeguard your operations and assets against potential cyberthreats. Because our approach is highly customized and grounded in transparency, when you work with us, you know exactly what you will end up with—and at what price.
Service tiers
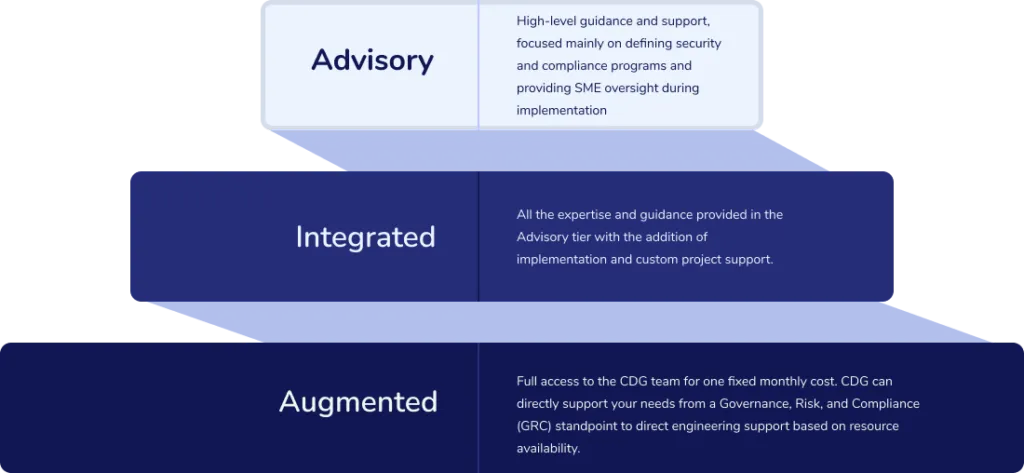
Cybersecurity as a service is broken down into three tiers – Advisory, Integrated, and Augmented. In all these tiers, Cyber Defense Group aims to provide strategic and tactical solutions, reduced cyber risk by increasing security control maturity, compliance with all regulatory requirements, address ongoing questions and issues around cybersecurity, and visibility to the board, C-suite, and other stakeholders around the risks, threats, and security maturity of the organization.
What to expect
An assessment is the first step in a Cybersecurity as a Service offering.
You will have monthly/bi-monthly meetings with our team.
Our team will assist you with representation to clients, customers, executives, and boards regarding security purposes
We are agnostic regarding tools, vendors, and solutions, ensuring the best product(s) for your unique business needs.

CDG's Cybersecurity as a Service ® offering may include:
Virtual Chief Information Security Officer (vCISO) team
Compliance readiness
AppSec/SDLC security
Program governance
Malware protection
Security training
DevSecOps
Incident response
Risk management
Asset management
Disaster recovery/business continuity
Logging and monitoring
Privacy & data controls
System hardening & segmentation
Vulnerability management
Identity and Access Management (IAM)
Security testing
Third-party security
Forensic investigations
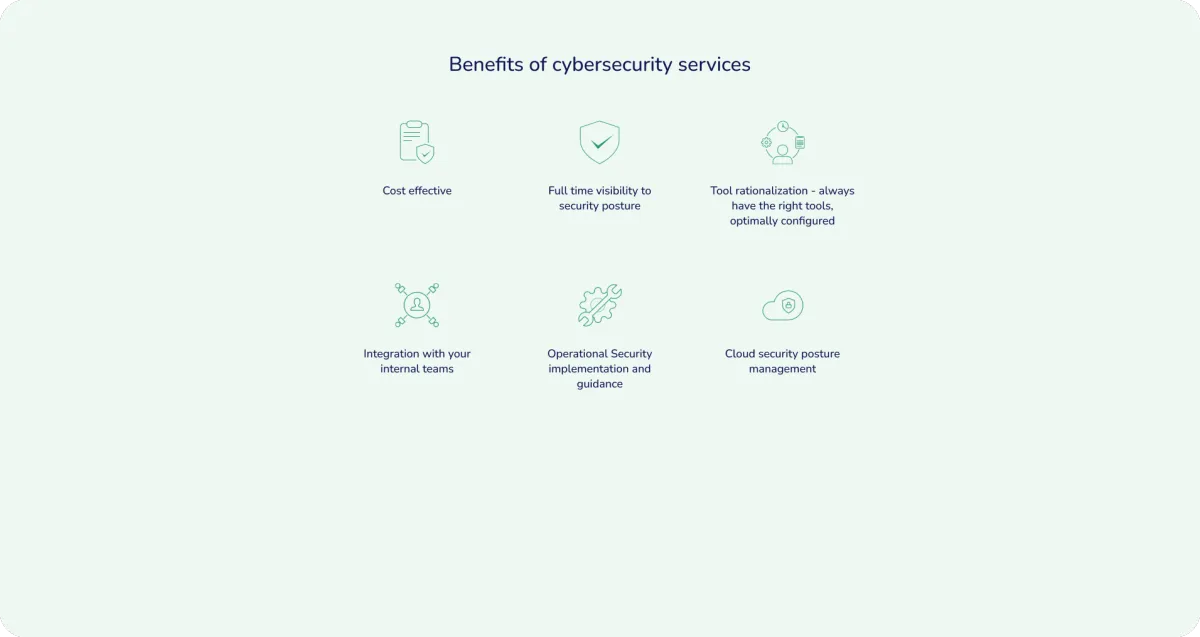
The benefits of a cybersecurity as a service
Demonstrable security that conveys strength to customers and a competitive advantage
Real-time visibility into your security posture
Actionable insights to help you address threats and risk to data
A rationalized suite of tools optimally configured to your business needs
Integrated security protocols across internal teams
Operational security implementation and guidance
Agile, cloud-focused security posture management
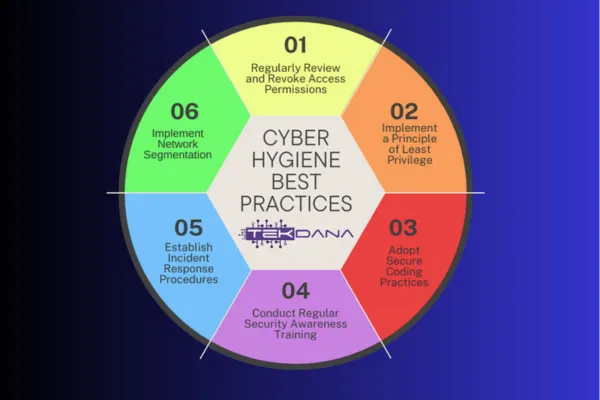
Cyber Hygiene Best Practices for Businesses
Cyber Hygiene Best Practices for Businesses
Essential Security Practices for Protection & Continuity. Disable AutoRun, implement web filtering, monitor network traffic, secure devices, and conduct security awareness training

Cyber hygiene refers to the practices and measures taken to maintain good cybersecurity. For businesses, it is essential as it protects sensitive data, preserves critical systems, and mitigates the risk of cyber attacks. By implementing strong passwords, updating software, and educating employees, businesses can reduce the likelihood of breaches. Below, we provide some key points of best practices to enhance your cyber hygiene.
Disable AutoRun/AutoPlay:
AutoRun and AutoPlay features, commonly found on operating systems, can automatically execute files from removable media such as USB drives. By disabling these features, you can prevent malware from spreading through unauthorized execution. This simple step significantly reduces the risk of malware infections and unauthorized access to your systems.
Implement Web Filtering:
Web filtering tools provide an additional layer of defense by blocking access to malicious or compromised websites. By carefully controlling internet access and filtering out potentially harmful content, you can minimize the risk of employees inadvertently visiting malicious sites that distribute malware or engage in phishing attacks.
Regularly Monitor Network Traffic:
Monitoring network traffic in real-time allows you to identify any unusual or suspicious activity that may indicate a malware infection or unauthorized access attempt. By leveraging network monitoring tools, you can detect and respond to potential threats promptly, mitigating their impact and preventing data breaches or system compromises.
Implement Application Whitelisting:
Application whitelisting is a proactive security measure that allows only authorized and trusted applications to execute on your company's systems. By explicitly defining a list of approved applications, you can prevent malicious software or unauthorized programs from running, significantly reducing the risk of malware infections and unauthorized system modifications.
Secure Mobile Devices:
Mobile devices have become an essential part of business operations, but their portability also makes them vulnerable to cyber threats. Implementing strong security measures on mobile devices, such as enforcing strong passcodes, enabling device encryption and using reputable security apps, helps protect sensitive company data and prevents unauthorized access in case of loss or theft.
Conduct Security Awareness Training:
One of the most critical aspects of cyber hygiene is educating employees about the risks they face and the best practices they should follow. Regular security awareness training sessions help employees recognize potential threats, such as phishing emails or suspicious websites, and empowers them to take appropriate actions to protect company data. By fostering a culture of cybersecurity awareness, you can significantly reduce the likelihood of successful cyber attacks.
Implementing these key points, businesses can significantly enhance their cybersecurity defenses. However, it's important to remember that cyber hygiene is an ongoing process that requires constant vigilance and adaptation to emerging threats. By consistently practicing good cyber hygiene, businesses can protect their digital assets, maintain customer trust, and ensure the continuity of their operations in an increasingly interconnected world.
Take The First Step Towards Cyber Resilience,
Get A Security Assessment Today!
Stay in the know, subscribe to our Newsletter.
SITEMAP
Solutions
Cloud Services (CSP)
Professional Services
Products
TekDana. All rights reserved 2024. Privacy Policy