
Cybersecurity-as-a-Service
Results-driven approach to cybersecurity.
Every business is unique, your security program
should be as well.
A Program Tailored to Your Unique Business Needs
Every 39 seconds, a cybersecurity attack occurs. In the event of a data breach, the consequences can be severe, including financial losses, legal liabilities, reputational damage, or even a complete business shutdown. From ransomware and phishing attacks to IoT, cloud, machine learning, and AI attacks — not to mention software vulnerabilities — businesses face a wide range of cyberthreats that require proactive and effective information security measures to mitigate.
At Cyber Defense Group, our sweet spot is designing Cybersecurity as a Service to help you stay one step ahead of today’s increasingly complex cybersecurity landscape and keep your business safe as you scale and grow. Our full-service cybersecurity Image team will help you strengthen your security posture so your business can proactively monitor, prevent, identify, investigate and respond to cyberattacks, 24/7.
How Cybersecurity as a Service Works
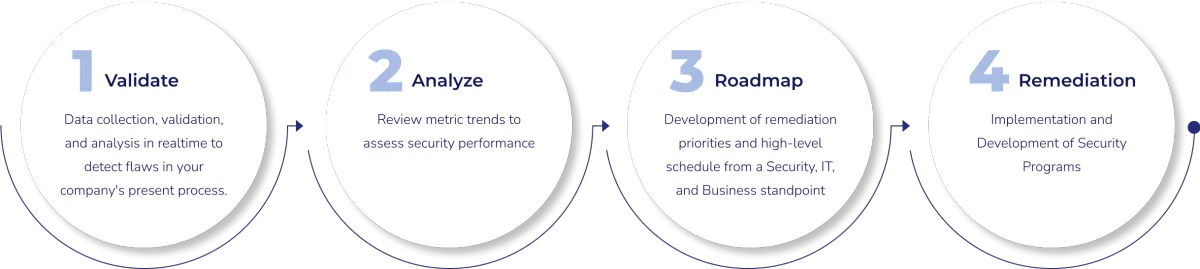
We work closely with you to understand your goals and priorities, then complete a comprehensive security assessment. Our findings are compared against regulatory and security frameworks to identify potential vulnerabilities and areas for improvement. From there, we design a customized security program that aligns with your needs — and rather than racking up billable hours, we outline a fixed-cost program to get you where you need to be.
This is not your typical consulting engagement. We train and work closely with your internal teams to ensure your growing business is equipped with the highest cybersecurity posture to safeguard your operations and assets against potential cyberthreats. Because our approach is highly customized and grounded in transparency, when you work with us, you know exactly what you will end up with—and at what price.
Service tiers
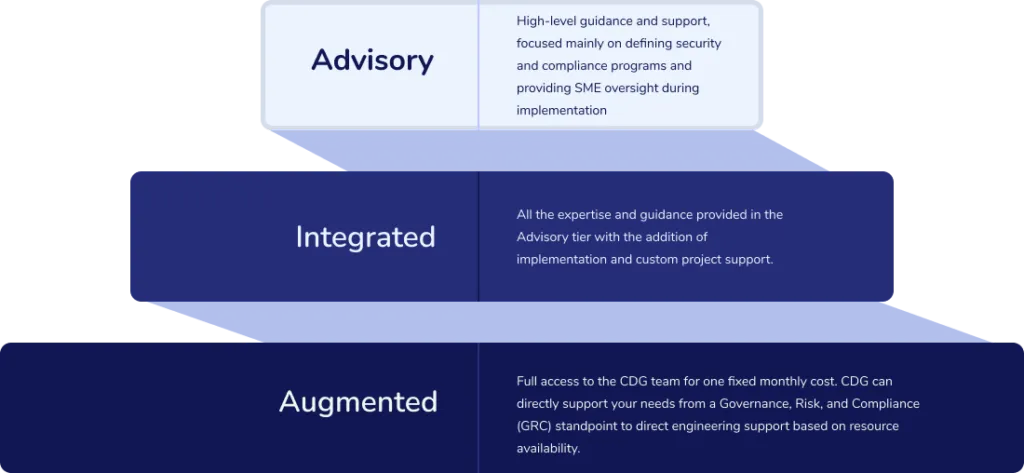
Cybersecurity as a service is broken down into three tiers – Advisory, Integrated, and Augmented. In all these tiers, Cyber Defense Group aims to provide strategic and tactical solutions, reduced cyber risk by increasing security control maturity, compliance with all regulatory requirements, address ongoing questions and issues around cybersecurity, and visibility to the board, C-suite, and other stakeholders around the risks, threats, and security maturity of the organization.
What to expect
An assessment is the first step in a Cybersecurity as a Service offering.
You will have monthly/bi-monthly meetings with our team.
Our team will assist you with representation to clients, customers, executives, and boards regarding security purposes
We are agnostic regarding tools, vendors, and solutions, ensuring the best product(s) for your unique business needs.

CDG's Cybersecurity as a Service ® offering may include:
Virtual Chief Information Security Officer (vCISO) team
Compliance readiness
AppSec/SDLC security
Program governance
Malware protection
Security training
DevSecOps
Incident response
Risk management
Asset management
Disaster recovery/business continuity
Logging and monitoring
Privacy & data controls
System hardening & segmentation
Vulnerability management
Identity and Access Management (IAM)
Security testing
Third-party security
Forensic investigations
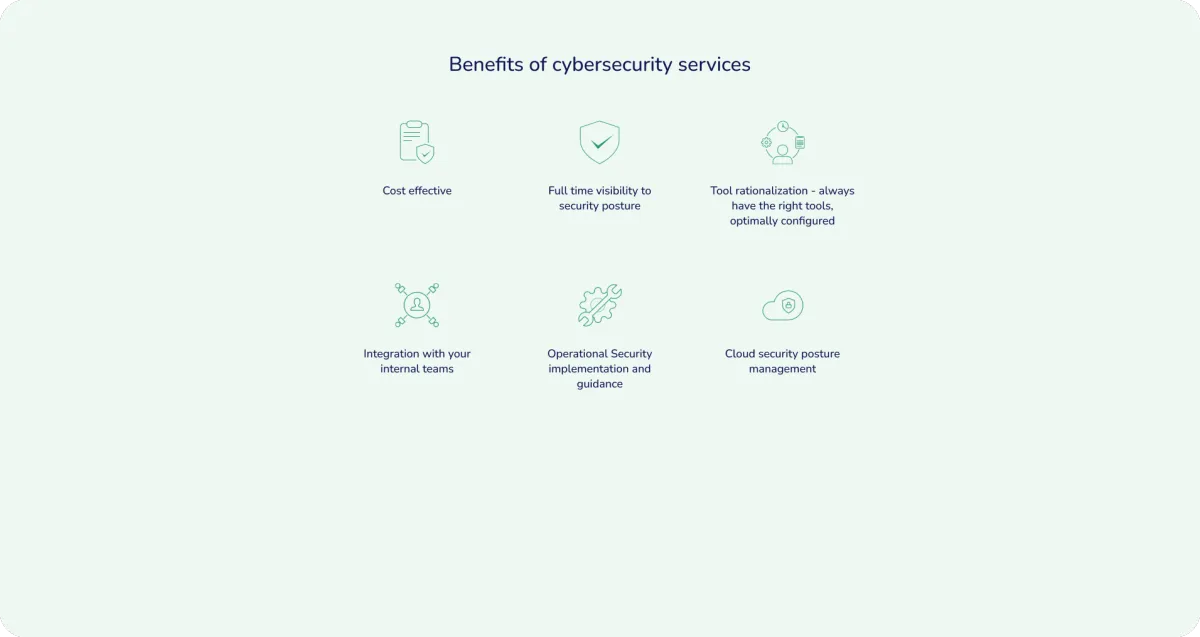
The benefits of a cybersecurity as a service
Demonstrable security that conveys strength to customers and a competitive advantage
Real-time visibility into your security posture
Actionable insights to help you address threats and risk to data
A rationalized suite of tools optimally configured to your business needs
Integrated security protocols across internal teams
Operational security implementation and guidance
Agile, cloud-focused security posture management

Safeguarding Nonprofit Cybersecurity and Donors Data
Safeguarding Nonprofit Cybersecurity and Donors Data
Learn practical strategies to safeguard nonprofit organizations from cyberattacks, fortify data privacy, and maintain the trust of donors. Discover the hidden risks nonprofits face in the digital world and take proactive steps to mitigate cyber threats.

Discover the hidden risks nonprofits face in the digital world and learn practical strategies to protect your organization from cyberattacks, ensuring the security of vital data and preserving the trust of your valued donors.
In today's digital age, nonprofits face a significant threat of cyberattacks. Despite assumptions that nonprofits are safe from hackers due to limited financial resources, the reality is quite the opposite. This article reveals the alarming truth about cyberattacks on nonprofits and provides practical steps to fortify data privacy and preserve the integrity of these vital organizations.
Contrary to popular belief, nonprofits are not immune to cyberattacks. Hackers target these organizations because they often lack robust cybersecurity measures and store valuable donor information. The consequences of a successful attack can be devastating, resulting in stalled projects, loss of credibility, and potential damage to the organization's reputation.
To effectively respond to cyberattacks, nonprofits must be able to identify the signs of a breach. Indications can include ransom messages, unusual website behavior, unauthorized social media posts, and unexplained password or email account changes. Vigilance and prompt action are crucial in mitigating the damage caused by an attack.
Once a cyberattack is detected, nonprofits should take swift action. This includes informing all relevant parties whose data may have been compromised, understanding legal obligations regarding data breaches, engaging forensic experts or cybersecurity professionals to assess the extent of the breach, and notifying local and federal authorities if necessary.
To safeguard against future attacks, nonprofits can implement several proactive measures. These include limiting the collection and retention of customer data, conducting regular staff training on cybersecurity awareness and best practices, restricting personal device usage on organizational networks, and investing in encryption software, firewalls, and cybersecurity solutions. Seeking a cyber security consultation can provide valuable insights and guidance tailored to the organization's specific needs.
Cybersecurity is critical for nonprofits and taking proactive steps to protect sensitive data and prevent attacks is essential. By recognizing the signs of an attack, swiftly responding to breaches, and implementing preventative measures, nonprofits can bolster their defenses against cyber threats. Remember, a cyber security consultation can provide valuable expertise and a comprehensive risk mitigation approach. By prioritizing cybersecurity, nonprofits can continue their invaluable work while safeguarding their mission and the interests of their supporters.
Do you know how to manage your cyber risk?
1st step: Train your people first.
2nd step: Take a cyber security risk assessment.
3rd step: Learn how to manage and mitigate your risk of being hacked.
Take The First Step Towards Cyber Resilience,
Get A Security Assessment Today!
Stay in the know, subscribe to our Newsletter.
SITEMAP
Solutions
Cloud Services (CSP)
Professional Services
Products
TekDana. All rights reserved 2024. Privacy Policy