
Cybersecurity-as-a-Service
Results-driven approach to cybersecurity.
Every business is unique, your security program
should be as well.
A Program Tailored to Your Unique Business Needs
Every 39 seconds, a cybersecurity attack occurs. In the event of a data breach, the consequences can be severe, including financial losses, legal liabilities, reputational damage, or even a complete business shutdown. From ransomware and phishing attacks to IoT, cloud, machine learning, and AI attacks — not to mention software vulnerabilities — businesses face a wide range of cyberthreats that require proactive and effective information security measures to mitigate.
At Cyber Defense Group, our sweet spot is designing Cybersecurity as a Service to help you stay one step ahead of today’s increasingly complex cybersecurity landscape and keep your business safe as you scale and grow. Our full-service cybersecurity Image team will help you strengthen your security posture so your business can proactively monitor, prevent, identify, investigate and respond to cyberattacks, 24/7.
How Cybersecurity as a Service Works
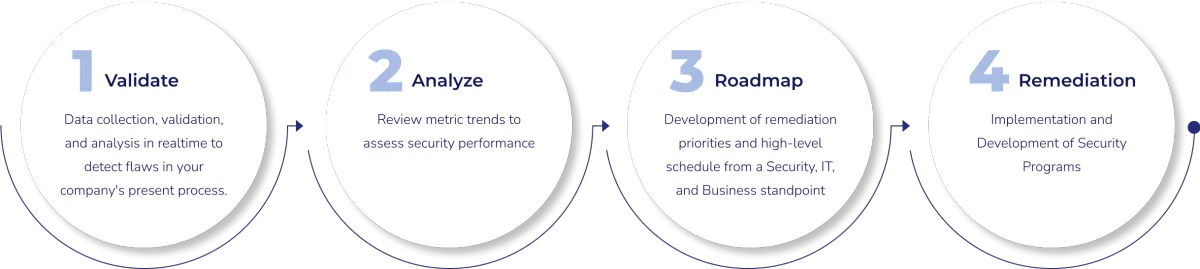
We work closely with you to understand your goals and priorities, then complete a comprehensive security assessment. Our findings are compared against regulatory and security frameworks to identify potential vulnerabilities and areas for improvement. From there, we design a customized security program that aligns with your needs — and rather than racking up billable hours, we outline a fixed-cost program to get you where you need to be.
This is not your typical consulting engagement. We train and work closely with your internal teams to ensure your growing business is equipped with the highest cybersecurity posture to safeguard your operations and assets against potential cyberthreats. Because our approach is highly customized and grounded in transparency, when you work with us, you know exactly what you will end up with—and at what price.
Service tiers
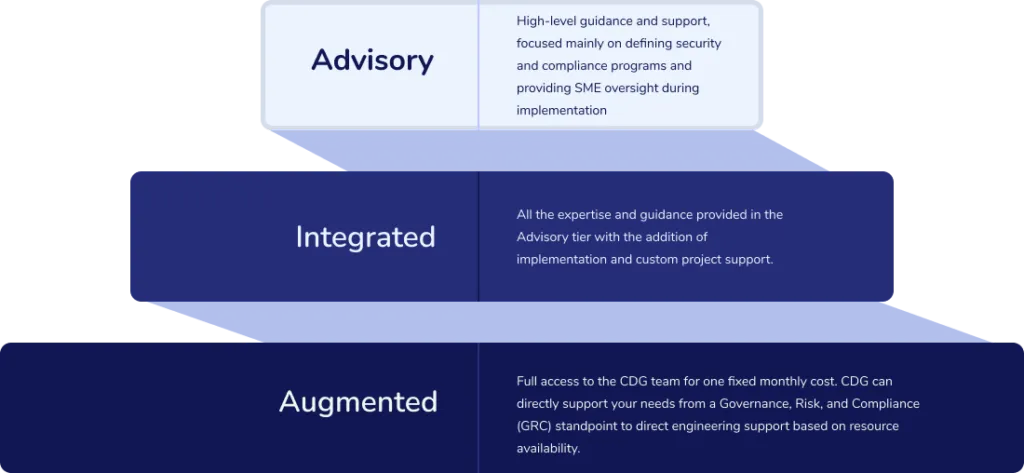
Cybersecurity as a service is broken down into three tiers – Advisory, Integrated, and Augmented. In all these tiers, Cyber Defense Group aims to provide strategic and tactical solutions, reduced cyber risk by increasing security control maturity, compliance with all regulatory requirements, address ongoing questions and issues around cybersecurity, and visibility to the board, C-suite, and other stakeholders around the risks, threats, and security maturity of the organization.
What to expect
An assessment is the first step in a Cybersecurity as a Service offering.
You will have monthly/bi-monthly meetings with our team.
Our team will assist you with representation to clients, customers, executives, and boards regarding security purposes
We are agnostic regarding tools, vendors, and solutions, ensuring the best product(s) for your unique business needs.

CDG's Cybersecurity as a Service ® offering may include:
Virtual Chief Information Security Officer (vCISO) team
Compliance readiness
AppSec/SDLC security
Program governance
Malware protection
Security training
DevSecOps
Incident response
Risk management
Asset management
Disaster recovery/business continuity
Logging and monitoring
Privacy & data controls
System hardening & segmentation
Vulnerability management
Identity and Access Management (IAM)
Security testing
Third-party security
Forensic investigations
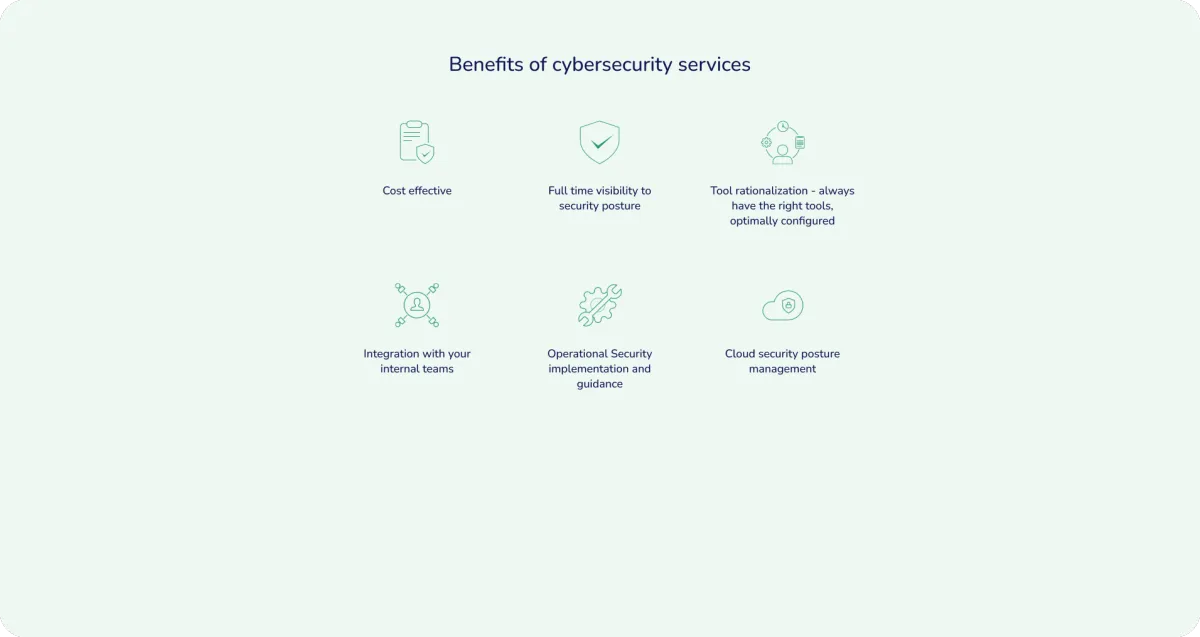
The benefits of a cybersecurity as a service
Demonstrable security that conveys strength to customers and a competitive advantage
Real-time visibility into your security posture
Actionable insights to help you address threats and risk to data
A rationalized suite of tools optimally configured to your business needs
Integrated security protocols across internal teams
Operational security implementation and guidance
Agile, cloud-focused security posture management

The Rising Threat of GenAI-Powered Phishing: Next-Gen MFA as the Ultimate Defense
The Rising Threat of GenAI-Powered Phishing: Next-Gen MFA as the Ultimate Defense
Urgent need for next-gen MFA. Cybercriminals leverage GenAI to craft convincing phishing attacks. Adopting wearable FIDO2 devices like Token Rings provides robust defense. Prioritize next-gen MFA to combat rising GenAI-driven threats.

If MGM, Johnson Controls, Chlorox, Hanes Brands, Caesars Palace, and so many others cannot stop the attacks, how will anyone else?
Phishing-driven ransomware is the cyber threat that looms larger and more dangerous than all others. CISA and Cisco report that 90% of data breaches are the result of phishing attacks and monetary losses that exceed $10 billion in total. A report from Splunk revealed that 96% of companies fell victim to at least one phishing attack in the last 12 months and 83% suffered two or more.
2023 witnessed a surge in ransomware incidents, emphasizing the urgent need for robust cybersecurity measures. Phishing-driven ransomware attacks have emerged as the most significant and perilous cyber threat, resulting in substantial data breaches and financial losses. As cybercriminals leverage Generative Artificial Intelligence (GenAI) to craft highly convincing phishing messages, traditional defenses are proving inadequate. This article explores the impact of GenAI on phishing attacks and highlights the role of next-generation Multi-Factor Authentication (MFA) as a powerful defense mechanism.
The Rise of GenAI-Powered Phishing:
Phishing attacks, exploiting human vulnerabilities rather than technological weaknesses, have become increasingly effective. With the advent of GenAI, cybercriminals now possess the capability to create incredibly persuasive and realistic phishing messages, making it challenging for users to discern between genuine and fake communications. The use of GenAI tools enables the automation of highly targeted phishing campaigns on a massive scale, bypassing traditional anti-phishing solutions that rely on pattern recognition.
The Ineffectiveness of Traditional Defenses:
Traditional phishing detection methods fall short in identifying GenAI-generated phishing messages, as they lack the usual signs of phishing, such as misspellings or generic language. Furthermore, cybercriminals can launch sophisticated phishing attacks without being hacking experts, thanks to GenAI tools. This raises concerns about the ability to detect and combat these super realistic fakes, signaling the need for a reevaluation of anti-phishing tactics.
The Power of Next-Gen MFA:
To combat the escalating threat of GenAI-powered phishing attacks, organizations are shifting their focus towards the next-generation MFA. This approach involves replacing traditional credentials and legacy MFA solutions with physical, wearable FIDO2-compliant devices. Next-gen MFA eliminates human factors in phishing attempts, making it virtually phishing-proof. These advanced biometric wearables not only protect against common vulnerabilities but also mitigate risks associated with BYOD devices and compromised credentials.
Defending Against the Phishing Ai:
Next-gen MFA devices, such as Token Rings, play a pivotal role in countering the impending tsunami of GenAI-powered phishing attacks. By rendering even, the most sophisticated phishing attempts ineffective, these wearable devices provide the best defense against the evolving threat landscape. Their constant proximity to the user ensures secure and immediate authentication, safeguarding sensitive information and thwarting attackers.
In conclusion, as the threat of GenAI-powered phishing continues to rise, it is crucial to prioritize the adoption of next-gen Multi-Factor Authentication (MFA) to safeguard your organization. By acknowledging the limitations of traditional defenses and embracing wearable FIDO2-compliant devices like Token Rings, you can establish an unmatched defense against the ever-evolving threat landscape. These advanced biometric wearables provide a robust barrier, rendering even the most sophisticated phishing attempts ineffective. To ensure the security of your organization in this era of GenAI-driven attacks, integrating next-gen MFA solutions is the proactive step needed to fortify your defenses and stay one step ahead of cybercriminals.
Take The First Step Towards Cyber Resilience,
Get A Security Assessment Today!
Stay in the know, subscribe to our Newsletter.
SITEMAP
Solutions
Cloud Services (CSP)
Professional Services
Products
TekDana. All rights reserved 2024. Privacy Policy